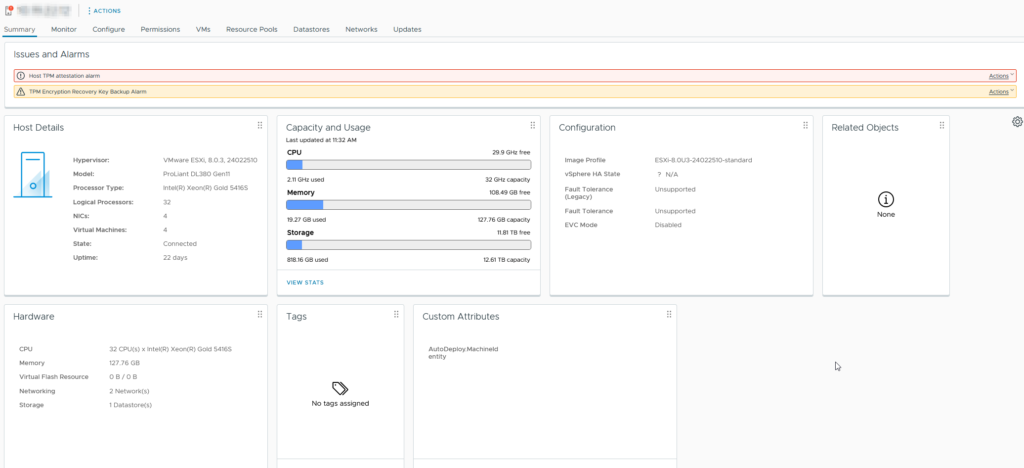
In the world of virtualisation, ensuring the security and integrity of your environment is paramount. VMware provides several mechanisms to enhance the security of ESXi hosts, one of which is the Trusted Platform Module (TPM) attestation. However, while using this feature, you may encounter the “Host TPM Attestation Alarm.” This article will delve into what this alarm means, why it occurs, and how you can resolve it.
What is TPM and TPM Attestation?
The Trusted Platform Module (TPM) is a hardware-based security feature that provides a tamper-resistant environment for generating, storing, and managing cryptographic keys used to verify the integrity of a system. In the context of VMware, TPM attestation is used to ensure that the ESXi host’s firmware and configuration have not been tampered with or modified in an unauthorised manner.
When an ESXi host with TPM is booted, it performs an attestation process, where the TPM generates cryptographic measurements of the host’s firmware, boot loader, and other critical components. These measurements are then validated against known-good values stored in a management entity like vCenter Server. If the measurements don’t match the expected values, the TPM attestation fails, triggering the “Host TPM Attestation Alarm.”
Why Does the ‘Host TPM Attestation Alarm’ Occur?
The “Host TPM Attestation Alarm” can be triggered for several reasons:
Firmware or BIOS Updates: If the host’s firmware or BIOS has been updated, the cryptographic measurements will change. If these new measurements haven’t been updated in vCenter Server, the attestation process will fail.
Host Configuration Changes: Any significant changes to the host’s configuration, such as boot order changes, modifications to secure boot settings, or updates to the ESXi host, can lead to a mismatch in the expected TPM measurements.
TPM Hardware Issues: Issues with the TPM chip itself, such as malfunctions or incompatibilities, can prevent proper attestation from occurring.
Incomplete or Incorrect TPM Configuration: If the TPM is not correctly configured in the BIOS or if there are issues with how the ESXi host is communicating with the TPM, the attestation will fail.
Mismatch in vCenter Server: If the vCenter Server has outdated or incorrect values for the expected TPM measurements, it may incorrectly flag a valid host configuration as a failure.
How to Resolve the ‘Host TPM Attestation Alarm’
Resolving the “Host TPM Attestation Alarm” requires a systematic approach to identify and address the underlying cause. Here’s how you can go about it:
Verify TPM and BIOS Configuration:
- Ensure that the TPM is correctly configured in the BIOS. This typically involves enabling TPM and Secure Boot. Depending on your server manufacturer, the exact steps may vary, so refer to the server’s documentation.
- Check that the TPM is active and functional. This can be done through the BIOS or UEFI interface.
Update Firmware and vCenter Measurements:
- If the host’s firmware or BIOS has been updated, ensure that vCenter Server has the latest measurements. You may need to re-establish trust by resetting the TPM or performing a fresh attestation.
- In vCenter Server, navigate to the host’s settings and initiate a reattestation process. This will allow vCenter to capture and store the new measurements as the “known-good” values.
Check Host Configuration:
- Review any recent changes to the host’s configuration. If changes have been made, ensure they are intentional and that vCenter has been updated to reflect these changes.
- Ensure that any updates to the ESXi host were properly executed and didn’t introduce inconsistencies.
Review vCenter Alarms and Logs:
- Check the vCenter logs and alarms for detailed information about the attestation failure. This can provide insights into whether the failure is due to firmware, configuration, or communication issues.
- In some cases, clearing the alarm and forcing a new attestation cycle can resolve transient issues.
Address TPM Hardware Issues:
- If the TPM chip itself is suspected to be faulty, you may need to replace the hardware. Before doing so, ensure that other potential causes have been ruled out.
- Ensure the TPM firmware is up to date. Some manufacturers release firmware updates specifically for TPM chips, which can resolve compatibility or functionality issues.
Reattestation and Validation:
- After addressing the potential causes, initiate a reattestation process. This can be done through the vCenter Server by navigating to the host’s security settings.
- Validate that the attestation process completes successfully and that the alarm is cleared.
Conclusion
The ‘Host TPM Attestation Alarm’ is an important security feature in VMware environments, signaling potential issues with the integrity of an ESXi host. While the alarm can be concerning, it is typically resolvable with careful review and updates to the host’s configuration, firmware, and TPM settings. By understanding the underlying causes and following a methodical approach to resolution, you can maintain the security and stability of your VMware environment.
If you regularly encounter this issue, consider setting up a maintenance schedule to verify and update the TPM configurations and measurements, ensuring ongoing trust in your ESXi hosts.