You’ve setup an active directory certificate authority and your browser isn’t trusting the certificates or they are showing as insecure.
There are a ton of articles out there about sharing the root certificates via group policy, so I will presume you’ve aready done that. If you haven’t, please do that first.
This article will cover the potential cause of the two below errors:
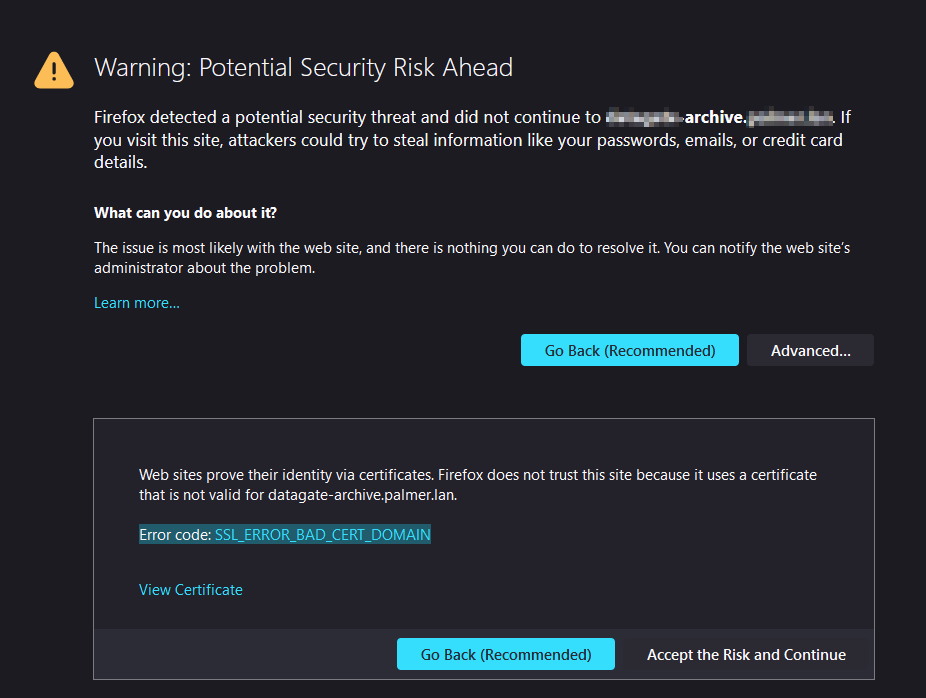
Firefox – Error code: SSL_ERROR_BAD_CERT_DOMAIN
Chrome – NET::ERR_CERT_COMMON_NAME_INVALID
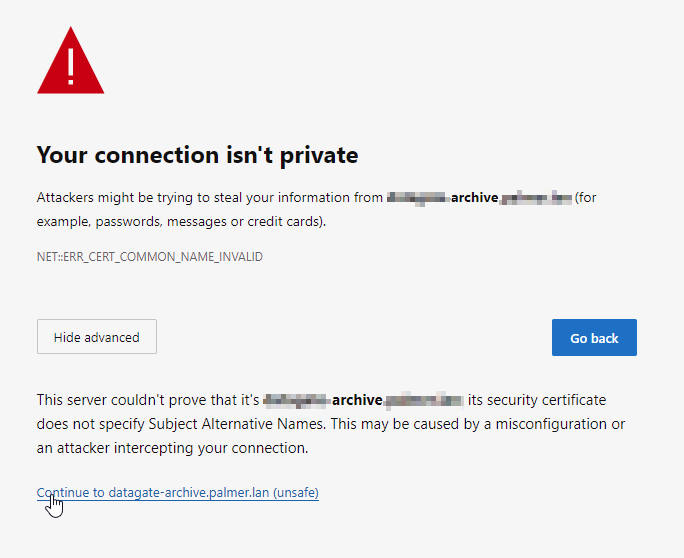
The reason for these errors is because the certificate doesname match the FQDN. For example, if the server is called server1, but your have an FQDN of website.domain.local then they won’t match, so the certificate is invalid.
This isn’t something you’ve conciously done, it’s down to the way that IIS requests the domain certificates.
How to request an active directory certificate with multiple FQDNs
To overcome the errors shown above, you just need to request a certificate via the Certificate MMC instead of the IIS MMC, but following the below steps:
1) Click ‘Start’
2) Select ‘Run’ (if you don’t see it, right click on the ‘Start’ button instead and select it from there)
3) Type ‘MMC’ and press enter
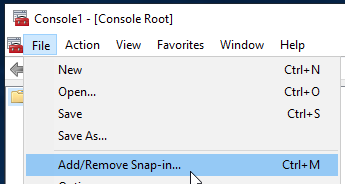
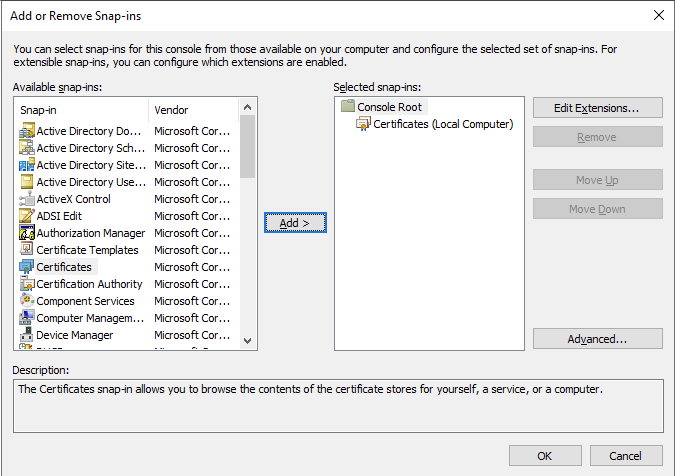
4) Select the ‘File’ menu, then ‘Add/Remove Snap-in’
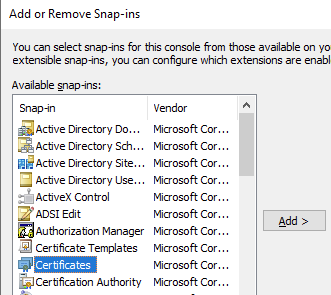
5) Select ‘Certificates’ and click ‘Add’
6) Select ‘Computer account’ and click ‘Next’
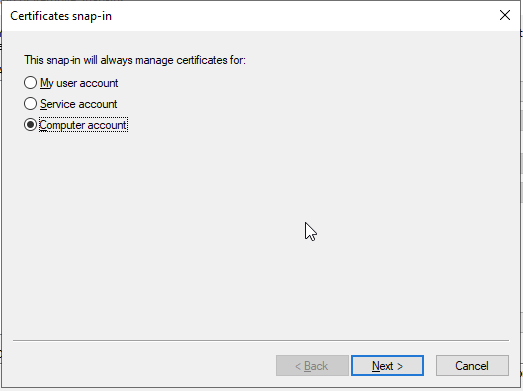
7) Select ‘Local computer’ and click ‘Finish’
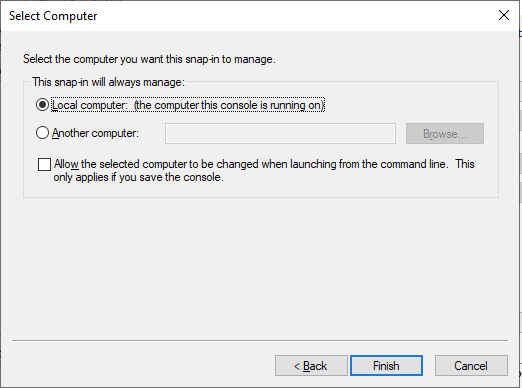
8) Click ‘OK’
9) Expand ‘Certificates’ and ‘Personal’
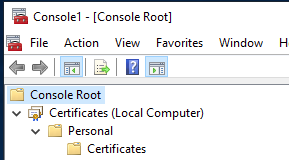
10) Right click on ‘Personal’, hover over ‘All Tasks’ and select ‘Request New Certificate’
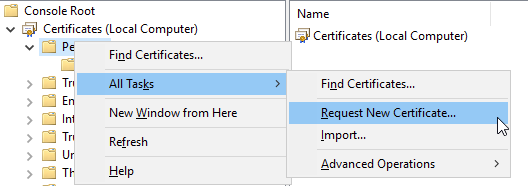
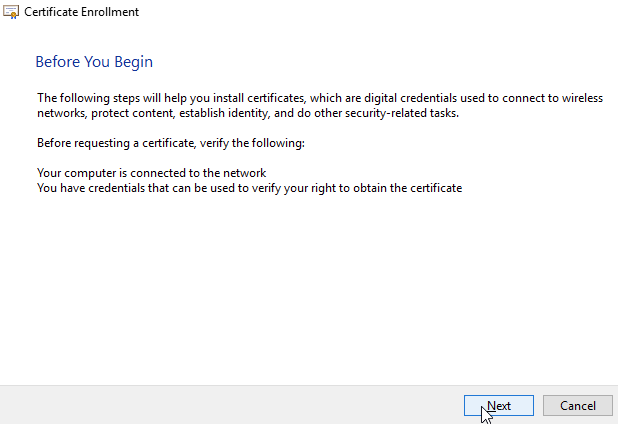
11) Click ‘Next’
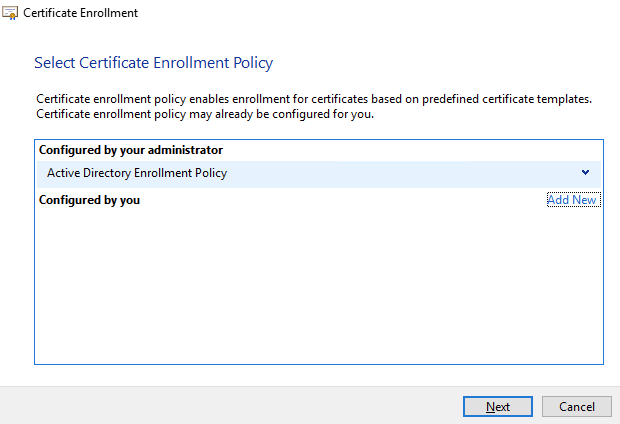
12) Click ‘Next’
13) Select ‘Web Server’ and then click ‘Details’ to the right of the web server row, to show the ‘Properties’ button.
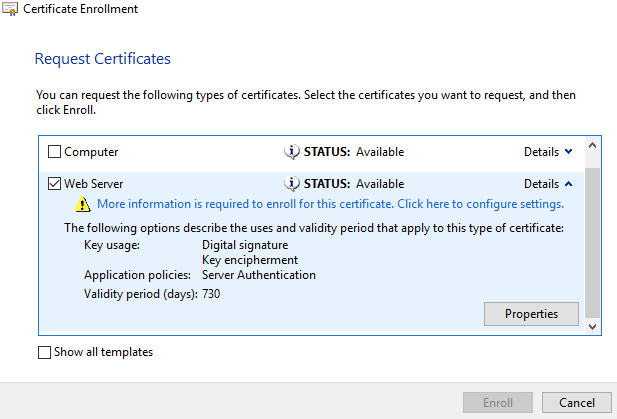
14) Click the ‘Properties’ button, as shown above
15) Select ‘common name’ as the type in the subject name area, and enter the FQDN of your server in the ‘Value’ box, and click ‘Add’
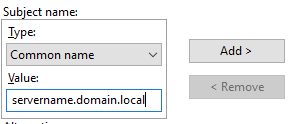
16) Then in the ‘Alternative name’ area, set the type to ‘DNS’ and add the FQDN of any other DNS aliases and click add. Repeat the process for each additional FQDN.
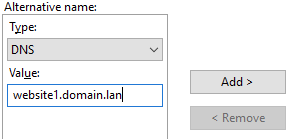
For example if you have another A record of website.domain.local pointing to the same server, mapped to a different IIS website, that’s where it comes in handy.
You should have somethings like this when done:
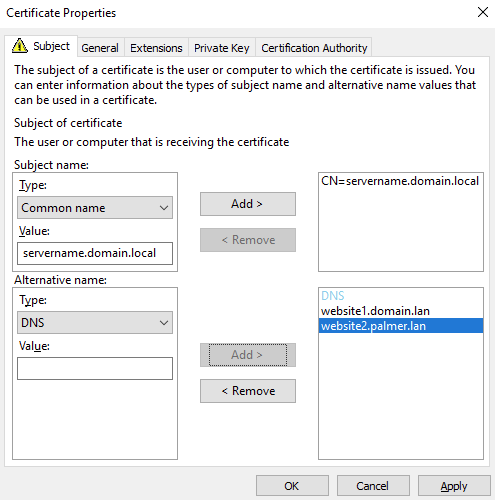
17) Click ‘OK’
18) Click ‘Enroll’
19) Click ‘Finish’
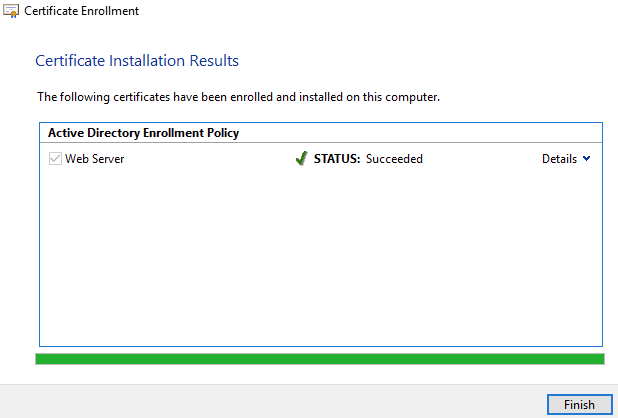
20) That’s it, you’ll now see the certificate in the Personal > Certificate area that you expanded earlier
Now you have that certificate on the server, go back into IIS and assign it via the website bindings.

Regular monitoring and maintenance can help keep your certificate services running smoothly!